Chameleon Tiny- Know All About The New-Age RFID Emulator
What is Chameleon Tiny Professional?
Radio Frequency Identification (RFID) is a technology that makes devices automatically identify the authentication by checking the stored information.
This particular concept made RFID so popular that, now we use RFID in various verticals such as contactless payments, electronic ID cards, automation & manufacturing, etc.
As part of the pen testing exercise, security professionals often get a situation where they have to read/clone an RFID card. In those situations, RFID tags become a crucial part of any project.
The Chameleon Tiny Professional is a very powerful RFID Emulation Device, capable of simulating multiple types of RFID Tag Formats in one very portable device.
The Chameleon Tiny Professional is a very small version of the ChamelonMini, designed as a keychain emulator for all your HF tags. During a pen test, sometimes the manipulation of RFID tags will be a crucial part of any project.
Chameleon Tiny Professional is a very discrete & powerful RF tags emulation tool will be a great addition to anyone’s arsenal. Compared to proxmark3, this tool is more versatile and stealthier in cracking, capturing & replaying.
Also, unlike the RevG (original) it can read cards from much more distance and also has low power sleep to support its small battery.

What makes Chameleon Tiny Professional Powerful?
-
RevG Framework-based
Chameleon Tiny Professional is based on the RevG Framework, and also very carefully optimized for performance, size, and portability.
-
Versatile for RFID Hacking
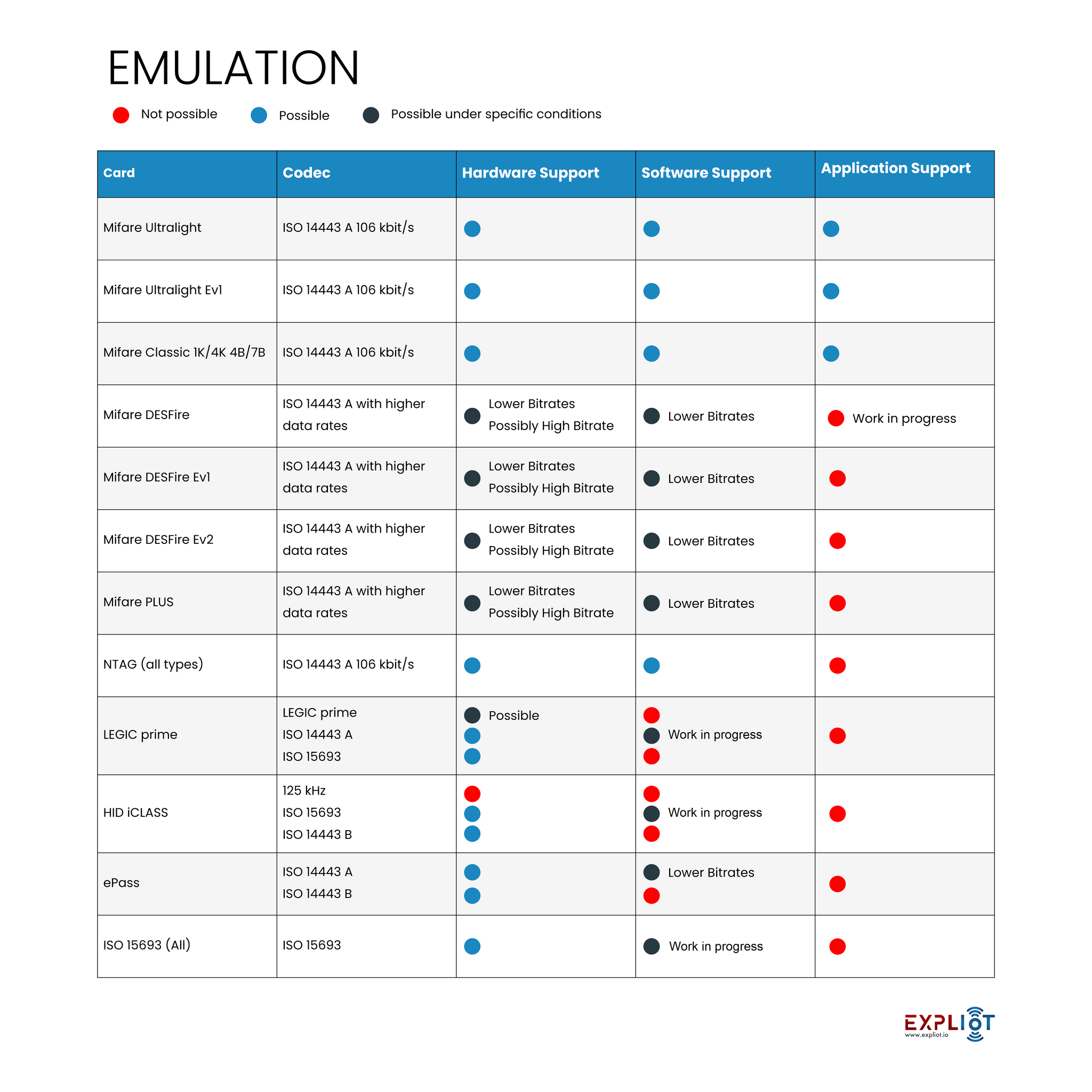
Chameleon Tiny Professional can emulate MIFARE Classic® (1k & 4k, with 4- and 7-byte UIDs) and MIFARE Ultralight® (Standard, EV1 80 and 164 bytes), Vicinity, SL2S2002, TiTag Standard, and EM4233. It can also sniff ISO15693 and ISO14443A cards.
-
Open-Source Support
One particular addition that makes tools a great choice is a long-term support; Chameleon Tiny Professional has a strong community of active development support which makes it more versatile for RFID Hacking.
Along with multiple chipset emulation, it can also crack MFKey32 protocol operating cards, in addition to UID sniffing, fuzzing, and manipulation. Chameleon Tiny Professional supports the MFKey32 attack ('Reader Attack'). This attack decodes the keys sent by the reader to check the validity of a card. Further stage these decoded keys can then be used to decode a target tag.
This type of attack is prominent in the latest generation of Mifare tags that have a hardened PRNG system. Using this tool, MFKey32 Attack can be performed via the Windows Chameleon UI tool, or via the Chameleon Android App.

How is Chameleon Tiny Professional malleable?
-
Cross-platform support
The Chameleon Tiny Professional is cross-platform (Windows / MacOS / Linux / Android) and can be configured and operated entirely over a serial connection / command-line interface.
-
Availability
There is also a Windows-based Chameleon UI tool, which allows for rapid configuration, dump transfer, and several useful analysis tools, for Android users can also control the Chameleon Tiny Professional via USB-C and the Official Chameleon Tiny Professional Android application. For Apple / iOS users "CT Manager" Application, is available on the Apple Store.
-
Controllability
The Chameleon Tiny Professional is controllable to save, restore, analyze and modify data dumps directly from the application. It also provides real-time device information. Users can also flash the tool when an upgrade is available independently by following the update instruction guide.


FAQ:
Is Chameleon Tiny Professional capable of writing cards?
Chameleon Tiny Professional professionals' hardware has capability to write cards. However, the current firmware of it does not support writing cards, as it was designed to emulate cards.
Can we make Chameleon Tiny Professional detect as Magic card?
Yes, users have an option to make the tool detectable as magic card.
Can I perform “Reader Attack” using this tool?
Yes, Chameleon Tiny Professional is capable of MFKey32 attack, in this attack, the keys sent by the reader are decoded and further used to decode a tag.
Mifare tags that have a hardened PRNG system are susceptible to the “Reader Attack”






